Cyber threats such as ransomware, identity theft, and data exfiltration, which traditionally target on-premise resources are now a growing problem for cloud storage services. As companies continue to deploy resources to the cloud, the need to address these additional security challenges is a major concern.
Data security and compliance
Everybody knows how the cloud has changed how businesses get work done. Being able to access files and folders outside of the four walls of the office is the norm for so many businesses now. Supercharged by the rush to remote working, most IT infrastructures are now a mix of on-premise and cloud-based solutions.
However, securing this cloud hybrid infrastructure only gets more complex. Particularly vulnerable are SMBs as they often lack the expertise and resources to effectively secure their hybrid environments.
“Businesses often come to us after they’ve been hit with ransomware, hoping that we can help them recover. The ‘it won’t happen to me’ mindset is still very real.”
Adam Nightingale, Managing Director at Lucid IT Solutions.
The Challenge to secure SMBs
The Verizon Data Breach Investigation Report highlights common challenges for SMBs. It’s not so much these exact reasons; lack of resources, lack of expertise, lack of information, lack of time, lack of training – although they are all very relevant and real. The common issue on why we are seeing SMB as an easy target is because there is a ‘lack of something’.

This is where Managed Service Providers (MSPs) can be invaluable in navigating that process.
MSPs can provide strategic guidance on solutions that best fit organizations. As an MSP, your potential customers will have a range of questions spinning around their heads.
- How can I choose a Managed Services supplier when everybody seems to be saying the same thing?
- How can you safeguard our data from theft?
- How can you help comply with regulations in our industry?
Understanding these concerns and providing expertise is where MSPs can help.
So what’s driving SMBs to believe their data is unsafe in the cloud?
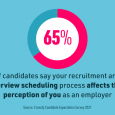
So although the benefits are clear, our research showed that 61% of SMBs still believe their data is insecure in the cloud. What is driving these perceptions?
Our research identified three key points.
- 1. Unauthorized access is harder to detect. With data stored on-premise, there is a need to be physically present in the office to access these files creating a natural barrier from outside the organization. Moreover, IT can restrict access only to specific devices. With cloud-based storage, data can be accessed from anywhere in the world and on any device, greatly increasing the likelihood of unauthorized access.
- 2. Data theft from employees leaving is harder to stop or prevent. For exactly the same reasons, it is much easier to spot an employee stealing valuable information when it is stored on the physical desktop computer. Cloud-storage makes it very easy for employees to steal data before they leave.
- 3. Organizations are still suffering breaches. Since moving to the cloud, 29% of organizations have suffered a breach of files or folders stored in the cloud. The consequences of breaches have been incredibly damaging — with 15% saying they have suffered significant reputational damage due to unauthorized access to sensitive corporate data stored on cloud networks.
MSPs are perfectly placed to help
Most MSPs and SMBs focus on protective security such as antivirus, patch management, email or web filters, application whitelisting, and perhaps two-factor authentication for just their most privileged accounts. There’s nothing wrong with this. These are obvious protection and prevention steps you should take, but it’s not enough to just put the barriers up.
Despite best efforts, compromise will continue to happen. Attackers improve, look for new ways to take advantage and the problem is no one is detecting this. And if no one is detecting, no one can respond.
In fact, sometimes the challenge with a breach is to know they even happened at all. According to the Ponemon Institute, it takes on average 191 days to discover a breach.
The best protective strategy, therefore, needs to be validated over time. ‘Detect and react’ should be used to ensure preventative measures are working – spotting and reacting to abnormal or suspicious activity.

Data protection starts with file access auditing
File Access is at the heart of data protection. Files and folders remain the first attack option. Unchecked access to files and folders puts companies at risk from theft, alteration or the deletion of sensitive data. Prohibiting any unauthorized access is what makes data protection possible.
[“source=isdecisions”]